In August, the computer systems of Prospect Medical Holdings—a company that operates 16 hospitals in four states and 166 outpatient clinics—were hobbled after a ransomware attack, the worst such attack in the United States so far this year.
In August, the computer systems of Prospect Medical Holdings—a company that operates 16 hospitals in four states and 166 outpatient clinics—were hobbled after a ransomware attack, the worst such attack in the United States so far this year.
Though none of PMH’s facilities are in Kentucky, Louisville-based Norton Healthcare officials confirmed a cyberattack in May this year, and another cyberattack siphoned $500,000 from Owensboro’s Economic Development Corp.
Even the federal government isn’t immune. News reports in mid-June revealed several federal agencies and several hundred corporations and organizations were hit in a global Russian-based cyberattack. And these organizations are far from alone.
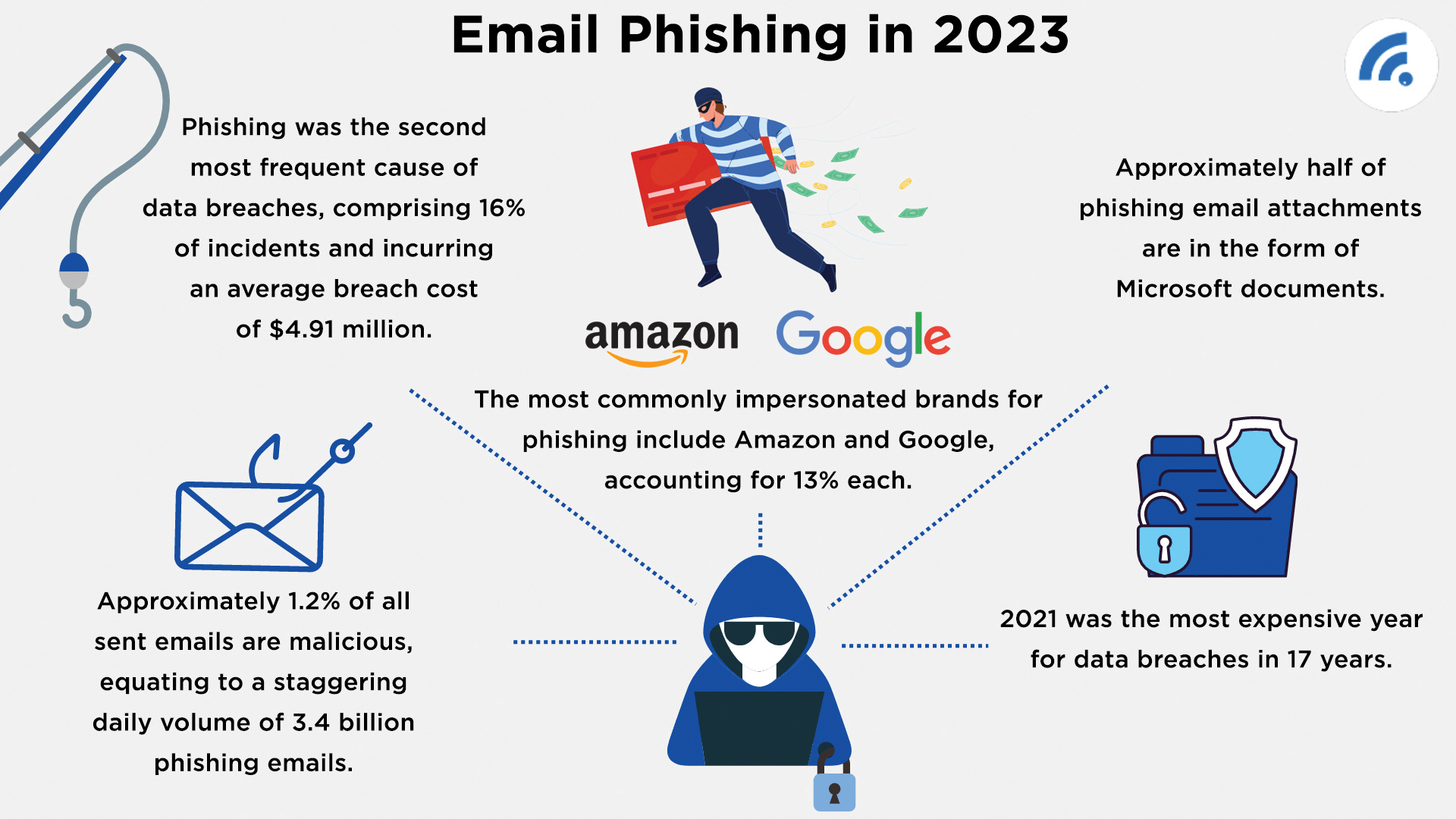
An IBM report shows the average global cost of a data breach in 2023 is $4.45 million—up 15% in the last three years—and notes that 51% of organizations plan to shore up security investments following a breach. The average savings for those who do, IBM says, is $1.76 million.
Kentucky cybersecurity experts say it is imperative that business leaders be aware of the most common scams and cyberattacks—as well as emerging threats—to develop a strong defense and a plan for the nearly inevitable breach.
Dana Howard, who works in the Lexington and Louisville law offices of Stoll Keenon Ogden as a member and attorney for data privacy and intellectual property litigation, said the firm’s clients hail from all business sectors, including healthcare. She likens the current cybersecurity situation to a war in which the defense improves, only for the offense to come back stronger, looking for weaknesses.
Scams abound—trust no one
Bad actors (or as we’ll call them here, BAs) often seek out human resources files, compromising employee credentials and stealing sensitive information those employees can access. Sites like LinkedIn can inadvertently assist by revealing who works in HR or finance, who feasibly has electronic medical records information and more.
Kathie McDonald-McClure is a partner in the law firm of Wyatt Tarrant & Combs and leads the firm’s data privacy and cybersecurity practice in addition to being a member of the healthcare service team. McDonald-McClure says, “Even if you don’t handle consumer personal information, you still have to be concerned with protecting the personal identifying information of your employees. The internet is just full of resources for bad actors to target individuals, particularly employees who may have access to confidential or personal information that’s held by the company or in the company’s network.”
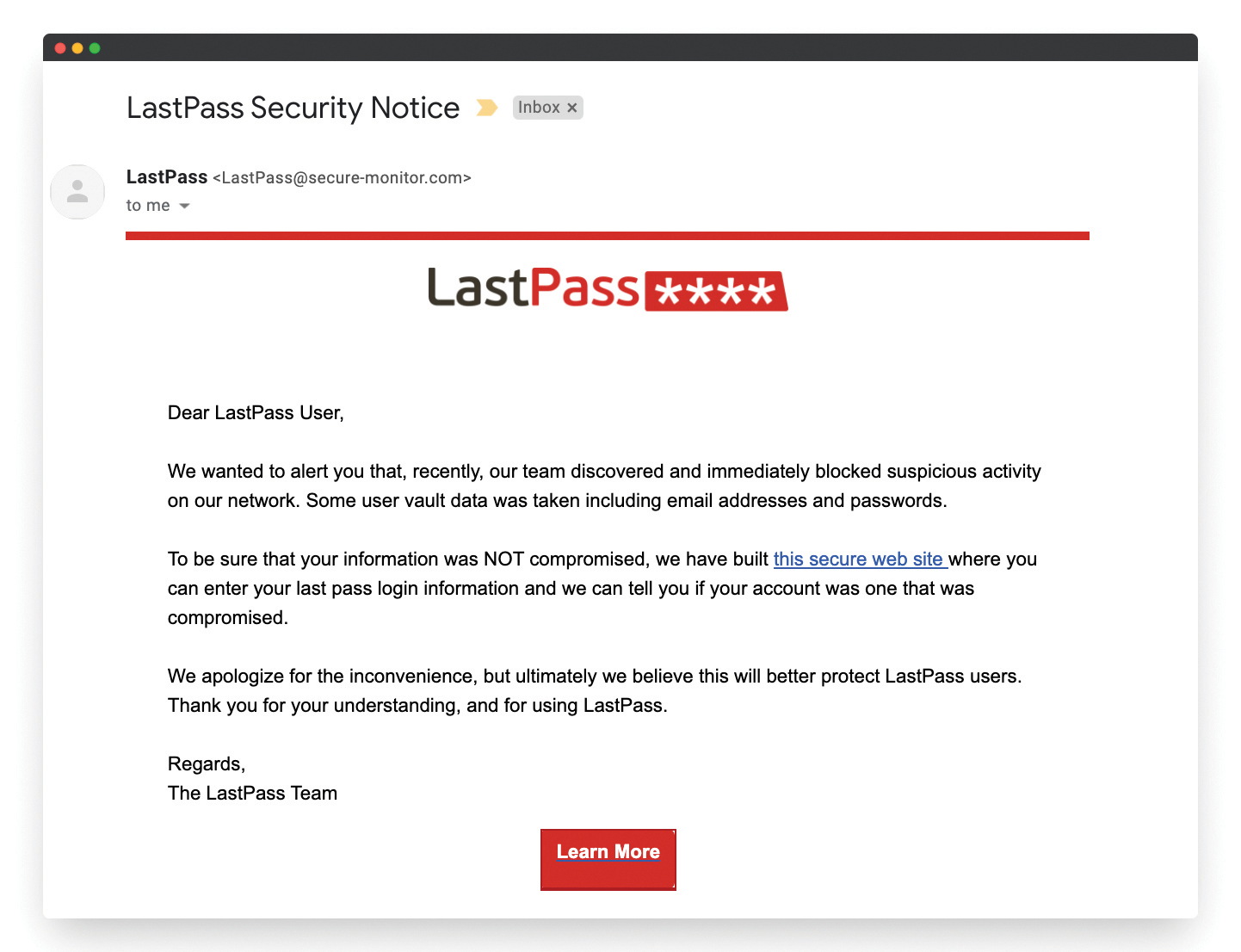
Emails are made to mimic authentic company communications and target HR representatives. Once those emails are opened, hackers can launch malware and gain access in a flash to W2 software and its sensitive contents, she said.
Oftentimes, she said, they’re purposely sent at busy times of the day when employees may be distracted or hurried—right before lunch or time to go home. The emails may address the individual by name and pretend to be another company official like a CFO, someone the employee would want to please with a timely response.
On closer inspection, the email may have minor details that go unnoticed in haste, such as a company URL that has an “i” instead of an “l” in the name.
Once they have broken into a company’s email, BAs may even send emails from a real employee’s account to fool vendors and others into wiring money to their own account, automatically deleting these messages from the “sent” folder to avoid detection.
McDonald-McClure says that when requests are made to change the routing of funds to a different account, it’s advisable to pick up the phone and verbally double check with suppliers to confirm such a request.
Other tricks are ransomware attacks against networks or employee mobile devices that when lost or stolen and unprotected by multifactor authentication can be mined for data by criminals.
“They can get access to a lot of information pretty quickly,” McDonald-McClure said.
Sometimes even a rogue employee will steal personal information from a company to pass along for personal gain, she added.
 The changing landscape
The changing landscape
Jon Salisbury is CEO of Newport-based Nexigen, a company founded in 2003 as a utility computing company before the term “cloud” existed. Nexigen now has a 24/7 operations center and provides remediation services if clients are attacked. Salisbury works primarily with companies that employ 10 to 2,000 people.
“We sell confidence as a service,” he said. “We don’t want to sell you fear. We don’t want to sell you doom and gloom.”
In the past, he said, BAs primarily hacked into companies’ networks to be disruptive rather than for monetary gain. But today, cyberattacks have become a whole business model for some, targeting both sensitive data and the employees with access to that data.
“The intent has changed, and now they definitely are focusing on ransoming or gathering that data and selling it on the black market,” Salisbury said.
He said the data of larger companies, like Kroger or Procter & Gamble, would be huge targets for the volume of valuable data, but those companies have the means to better secure their networks, making them more complicated to infiltrate.
Meanwhile, smaller companies that maintain a lot of customers’ personal and financial data—like banks, mortgage companies, insurance companies and wealth management groups with 20-100 employees and limited budgets to spend on cybersecurity measures—may have increased appeal for BAs and are therefore more at risk, he cautions.
Salisbury said if one person in a company falls prey to an email-based phishing hack, in which a BA sends an email that looks like it’s from a trusted sender, a BA could leverage that information across multiple platforms, ultimately gaining access to identity management systems and using gleaned information to access other data repositories like logins to Salesforce or other applications.
Along with phishing, token hijacking, AI voice cloning and even image cloning of people can be used to dupe trusting employees into thinking they’re talking to someone they’re not, Salisbury said.
Black market pays for data
He said selling consumer data on the black market remains lucrative, going for as much as $180 per record for personally identifiable records and $360 for medical records that fall under federal privacy laws.
For a hospital with thousands of patients and multiple records for each person, that can really add up.
Salisbury notes that even a small business might have more than 100,000 records and their data may be worth more on the black market than the value of the business itself. To thwart the BAs, Salisbury said AI machine learning can help recognize unwanted behaviors.
Shane Ensminger, senior vice president/director of Central Bank’s financial intelligence and security unit, said banks are highly regulated, with strict security standards, resulting in good defense levels against cyberattacks. As a result, criminals often turn to the consumer, tricking some into divulging account information.
“Call spoofing scams, romance scams, business email compromises (BEC), tech scams, lotto scams, work-from-home scams, car-wrap advertising scams, real estate scams, social engineering and many other tactics are specifically designed to trick bank-account holders into giving up information or access to their bank accounts,” Ensminger said. Some criminals use combinations and layers of different types of scams to perpetrate their ruses and part unsuspecting customers from their money.
16 critical targets
His advice is to never trust caller ID. If you receive a call from a “banker” inquiring about suspicious activity it may be legit, but it’s best to end the conversation and then call your bank directly using the number listed on your debit or credit card or the bank’s trusted website to inquire.
Sarah Spurlock, co-chair of Stites & Harbison’s privacy and data security group and a member of the healthcare service group, helps a variety of business sectors prevent and respond to cybersecurity intrusions.
She and others assist with policies and procedures, erecting safeguards to protect personal information and the security of systems. They also create incident response plans, perform contract management, and review and assess breach responses and related legal obligations. In addition, the firm defends and responds to state and federal government investigations into data breaches, defends any lawsuits brought by those impacted by a breach, and can advise post-breach on steps to create new policies to prevent them from reoccurring.
Spurlock said the federal government has identified 16 critical infrastructure sectors like finance, healthcare, IT, water and wastewater systems that must be defended from cybersecurity attacks.
Though regulations are still being finalized, Spurlock said they will require notification within 72 hours if a business in one of these categories has experienced a cybersecurity attack, and within 24 hours if a ransomware payment has been made, regardless of whether personal information has been compromised.
The Security and Exchange Commission has also announced new rules for public companies that require a report within four days of a cybersecurity breach.
“I think that is pointing to a growing understanding that these attacks can be disruptive to businesses and critical operations,” apart from compromising people’s personal information, Spurlock said.
The cost of responding to an attack comes in a variety of forms: reduced productivity, negative public attention, investigations and litigation, all of which can take some time to fully remedy.
Steps to keep your system safer
At assurance, advisory and tax services firm FORVIS, Louisville-based Matt Smith is a partner leading IT risk/compliance. Smith works collaboratively with Charlotte-based Principal Tom Tollerton to serve a wide variety of cybersecurity needs for clients.
Smith focuses on external and internal audits and Tollerton works more in compliance and technical risk, ethical hacking simulation testing and compliance for the industry. Both help clients detect and prevent cyberattacks like financial credit card data theft and compromised business emails.
“When you think of cybersecurity, it’s not just a technical matter,” Smith said. “The human element can’t be underestimated there, so training and education is a huge piece of that. Knowing your third parties and doing due diligence with third parties is a big piece.”
Tollerton said having policies and procedures for authentication, callbacks and dual signoffs on particular transactions can help, as can technical controls—automated solutions that detect unusual transaction requests that can then be flagged, put on hold and investigated until validated.
Be current on all updates
Wyatt, Tarrant & Combs’ McDonald-McClure recommends that companies of all sizes sign up to receive governmental Cyber Intelligence Security Agency (CISA) alerts and educational materials. She encourages IT vendors to do the same and to notify officials of potential issues.
Staying current on security updates from Microsoft and others is also important, she noted. And for healthcare providers of all kinds, the U.S. Department of Health and Human Services offers resources for feasible cybersecurity safeguards and employee training materials at 405d.hhs.gov.
Howard said Stoll Keenon Ogden helps clients formulate data breach response plans. Plans may include identifying who within the organization needs to be involved in breach response and next best steps when problems do arise. The response plan includes guidelines for creating or changing employee passwords, outlines approved uses of mobile devices, requires multiple signoffs for payments, and dictates who has approved access to sensitive information. The plan also addresses the need for cybersecurity insurance coverage.
The firm also helps clients become familiar with legal obligations of breach response, not only in Kentucky but in other states where affected customers may live or vendors may work. For example, some states require companies to provide credit monitoring services for impacted individuals.
McDonald-McClure said a decade ago, 25% of clients had cybersecurity liability insurance but that’s increased as that type of insurance has become more commonplace, with more agents/brokers to assist companies in securing policies and commercial general liability coverage starting to exclude such events.
Still, said McDonald-McClure, it can be fairly expensive for premium cybersecurity coverage, especially for companies that handle a lot of personal consumer data.
Insurers often require the business or individual to certify that they have certain measures in place, i.e., computer systems are segmented or multifactor identification is used. Insurers may also have their own lists of preferred forensic investigators and attorneys companies can use, she said.
 The plan could also include conducting a “mock breach” to gauge effectiveness and familiarize employees with response processes.
The plan could also include conducting a “mock breach” to gauge effectiveness and familiarize employees with response processes.
“It takes you a couple of hours, but practice makes perfect,” Howard said. “If anything, it makes people more calm when the actual situation happens.”
Howard said a federal data security/privacy mandate may be forthcoming, but meanwhile, some states are already passing their own legislation, some with cybersecurity components beyond those in the Data Breach Notification Act.
“I think we will see more states adopt those comprehensive statutes that really put a lot more onus on the businesses to know what data they have, know where they’re keeping it, and making sure they only keep data that they need to keep,” she said.